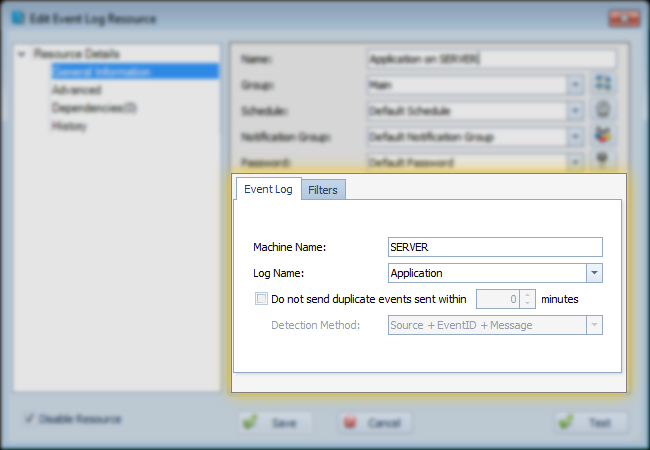
- Machine Name: This is the computer which you'd like to monitor the event logs from. This can be any computer on your LAN that you have administrative access to, using the password specified above. Once you enter/change this value, the next field is automatically updated with the logs available on this computer.
- Log Name: This is the event log on the computer you entered above. This should list all event logs, including the extended event logs added in W2K8.
- Do not send duplicate events within: When checks, Overseer will not send duplicate events if the same event occurred previously within the specified number of minutes.
- Detection Method:
- Source + EventID + Message - When selected, a duplicate event will be determined as an event matching the source name, event ID, and the exact message.
- Source + EventID - When selected, a duplicate event will be determined as an event matching the source name and event ID, even if the exact message is different. This is useful if the messages contain timestamps or numbers that change each time.
See Also:
Copyright 2003-2012 Sensible Software, Inc. All Rights Reserved.
Network Monitoring Software